web
bruteforce1_EzLogin
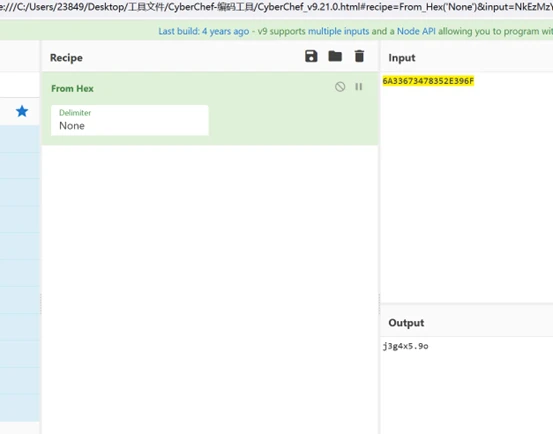
打开 http://111.74.9.131:10075 后随便输入用户名和密码用burp拦截抓包进行暴破
得到flag
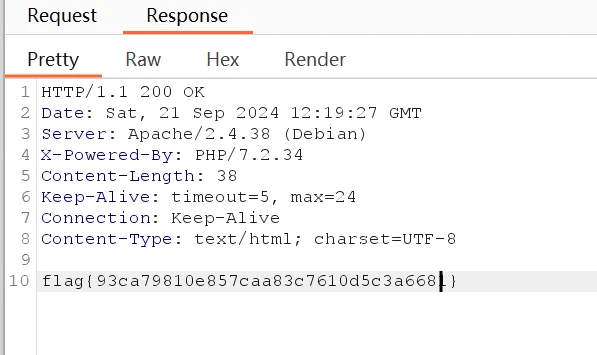
flag{93ca79810e857caa83c7610d5c3a6681}
token
访问’/robots.txt’得到源码
<?php
include 'flag.php';
session_start();
$_SESSION['seed']='xxxxxxxxxxxxxxxxx';
function createToken(){
mt_srand($_SESSION['seed']);
$dic = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ";
$token = '';
for ( $i = 0; $i <20; $i++ ){
$token .= substr($dic,mt_rand(0, strlen($dic) - 1), 1);
}
$_SESSION['token']=$token;
$top10=substr($token,0,10);
echo '<p class="p1">Generate token successfully</p><p class="p2">提示:您的令牌前10位为:'.$top10.'</p>';
}
createToken();
if(isset($_POST['token'])){
if($_POST['token']==$_SESSION['token']){
echo '<p class="p2">令牌验证成功,这是你想要的:'.$flag.'</p>';
}else{
echo '<p class="p2">令牌验证失败</p>';
}
}
?>
可以由给出的前十位得到seed,使用./php_my_rand
参数用下面脚本生成
str1='0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'
str2='R9WLuE5hGV'
length = len(str2)
res=''
for i in range(len(str2)):
for j in range(len(str1)):
if str2[i] == str1[j]:
res+=str(j)+' '+str(j)+' '+'0'+' '+str(len(str1)-1)+' '
break
print(res)
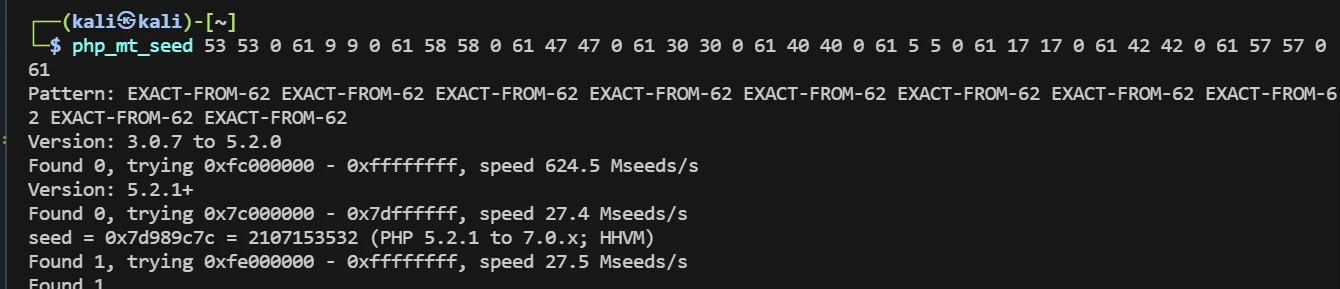
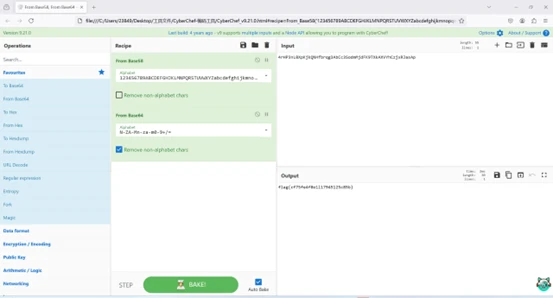
可以得到seed,将seed带入运行即可得到token
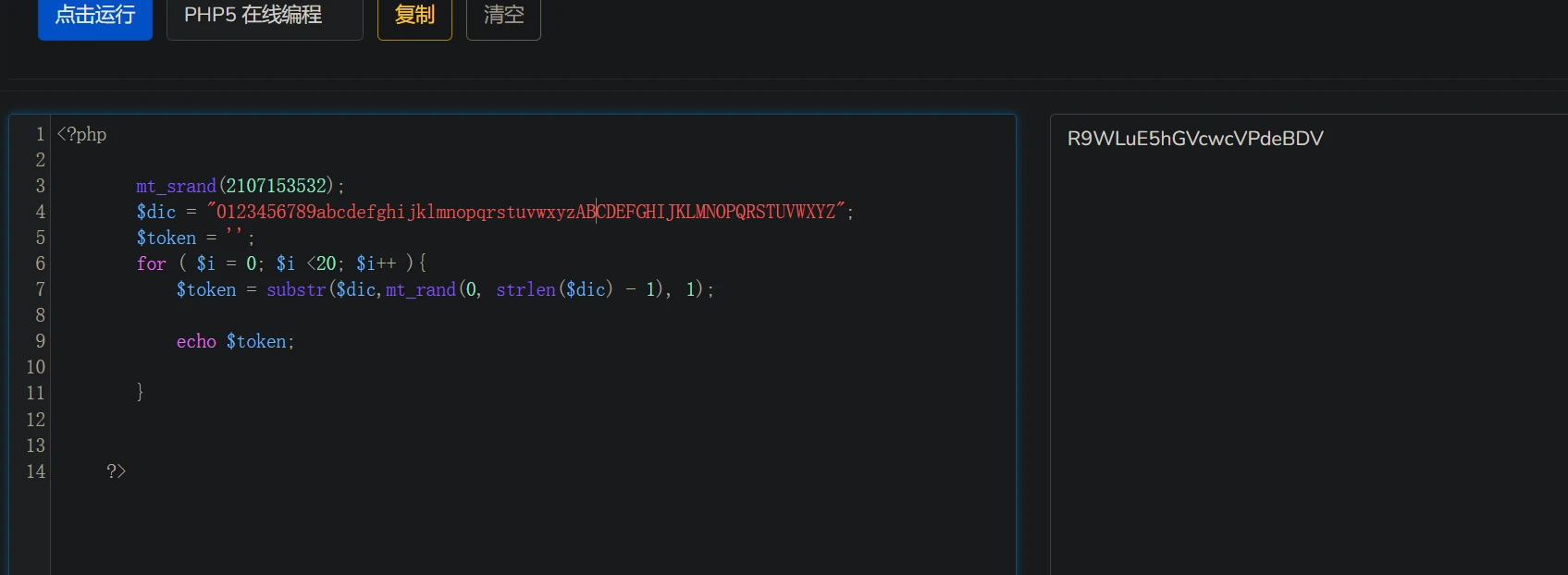
再用以下代码在php 版本为 5.2.x中运行即可得到key
<?php
mt_srand(2107153532);
$dic = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ";
$token = '';
for ( $i = 0; $i <20; $i++ ){
$token = substr($dic,mt_rand(0, strlen($dic) - 1), 1);
echo $token;
}
?>
reverse
xor
IDA64位打开得到文件
int __cdecl main(int argc, const char **argv, const char **envp)
{
char b[29]; // [rsp+20h] [rbp-50h] BYREF
char a[29]; // [rsp+40h] [rbp-30h]
int i_0; // [rsp+68h] [rbp-8h]
int i; // [rsp+6Ch] [rbp-4h]
_main();
a[0] = 116;
a[1] = 126;
a[2] = 115;
a[3] = 117;
a[4] = 105;
a[5] = 70;
a[6] = 122;
a[7] = 123;
a[8] = 97;
a[9] = 77;
a[10] = 123;
a[11] = 97;
a[12] = 77;
a[13] = 115;
a[14] = 77;
a[15] = 119;
a[16] = 115;
a[17] = 97;
a[18] = 107;
a[19] = 77;
a[20] = 96;
a[21] = 119;
a[22] = 100;
a[23] = 119;
a[24] = 96;
a[25] = 97;
a[26] = 119;
a[27] = 111;
a[28] = 18;
scanf("%s", b);
for ( i = 0; i <= 28; ++i )
b[i] ^= 0x12u;
for ( i_0 = 0; i_0 <= 28; ++i_0 )
{
if ( a[i_0] != b[i_0] )
{
printf("Wrong!!!");
return 0;
}
}
printf("you are right!!");
system("pause");
return 0;
}
所以我们需要编写程序得到用户的输入
编写代码为:
#include <stdio.h>
int main() {
// 初始化数组 a
char a[29] = {116, 126, 115, 117, 105, 70, 122, 123, 97, 77,
123, 97, 77, 115, 77, 119, 115, 97, 107, 77,
96, 119, 100, 119, 96, 97, 119, 111, 18};
// 用于存储用户输入的原始字符
char original[29];
// 逆向加密操作(异或 0x12)
for (int i = 0; i < 28; ++i) {
original[i] = a[i] ^ 0x12;
}
// 打印原始用户输入
original[28] = '\0'; // 确保字符串以 null 结尾
printf("Original input: %s\n", original);
return 0;
}
得到flag
flag{This_is_a_easy_reverse}
misc
TheCutestPeople
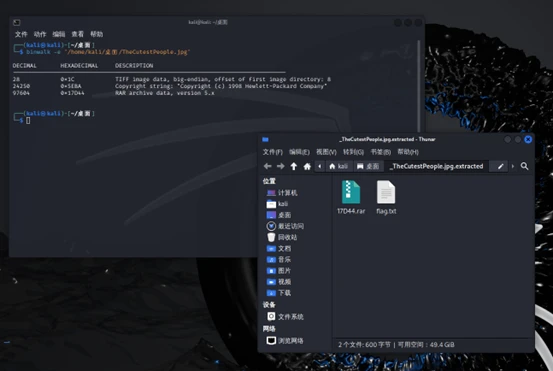
利用binwalk指令对文件进行分离得到flag.txt文件
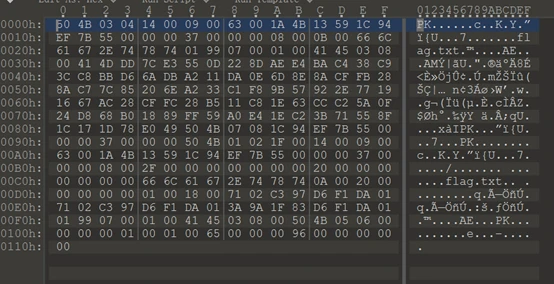
查看文件的十六进制发现是反着的
利用代码进行正序
with open(‘flag.txt’,’rb’) as f1, open(‘flag1.txt’,’wb’) as f2:
f2.write(f1.read()[::-1])
可以看到output里面生成了随机数,可以利用生成的随机数猜测后面的key,这里flag是先生成,所以可以倒序输入生成随机数,即可预测flag
#!/usr/bin/python3
from random import Random
def inverse_right(res,shift,bits=32):
tmp = res
for i in range(bits//shift):
tmp = res ^ tmp >> shift
return tmp
def inverse_left_values(res,shift,mask,bits=32):
tmp = res
for i in range(bits//shift):
tmp = res ^ tmp << shift & mask
return tmp
def inverse_right_values(res,shift,mask,bits=32):
tmp = res
for i in range(bits//shift):
tmp = res ^ tmp>>shift & mask
return tmp
def inverse_left(res,shift,bits=32):
tmp = res
for i in range(bits//shift):
tmp = res ^ tmp << shift
return tmp
def backtrace(cur):
high = 0x80000000
low = 0x7fffffff
mask = 0x9908b0df
state = cur
for i in range(3,-1,-1):
tmp = state[i+624]^state[i+397]
# recover Y,tmp = Y
if tmp & high == high:
tmp ^= mask
tmp <<= 1
tmp |= 1
else:
tmp <<=1
# recover highest bit
res = tmp&high
# recover other 31 bits,when i =0,it just use the method again it so beautiful!!!!
tmp = state[i-1+624]^state[i+396]
# recover Y,tmp = Y
if tmp & high == high:
tmp ^= mask
tmp <<= 1
tmp |= 1
else:
tmp <<=1
res |= (tmp)&low
state[i] = res
return state
def recover_state(out):
state = []
for i in out:
i = inverse_right(i,18)
i = inverse_left_values(i,15,0xefc60000)
i = inverse_left_values(i,7,0x9d2c5680)
i = inverse_right(i,11)
state.append(i)
return state
f = open("output","r").readlines()
c = []
for i in range(1000):
c.append(int(f[i].strip()))
partS = recover_state(c)
state = backtrace([0]*4+partS)[:624]
# print(state)
prng = Random()
prng.setstate((3,tuple(state+[0]),None))
flag = "flag{" + ''.join(str(prng.getrandbits(32)) for _ in range(4)) + "}"
print(flag)
即可得到flag